Using Resilient Secrets with the Delinea Platform
Secret Server offers Resilient Secrets for organizations to protect and recover their IT infrastructure and data as part of an overall disaster recovery strategy.

YouTube
Just in Time Permissions Explained #Delinea #PAM #CyberSecurity
Mastering Secrets Management: Best Practices for Secure Access Control
Secrets Management Best Practices
Explore comprehensive guides on how to securely manage and protect your organization’s secrets, ensuring robust access control and minimizing risk.
Integrations Made Easy
Step-by-step tutorials show you how to seamlessly integrate secrets management with popular platforms like Kubernetes, HashiCorp Vault, and AWS Secrets Manager.
Real-World Success Stories
Learn from detailed case studies highlighting how leading organizations implement secrets management to enhance security and compliance.
Stay Ahead of Cyber Threats
Get the latest updates on cybersecurity threats related to credential leaks and privileged access, keeping you informed and prepared.
Emerging Technologies in Secrets Management
Discover cutting-edge innovations and analysis on how new PAM and secrets management technologies are reshaping security strategies.
Compliance Made Simple
Access practical compliance guides tailored for GDPR, PCI-DSS, SOC2, and other regulations focusing on protecting secrets and credentials.
Risk Assessment Tools
Use downloadable checklists to evaluate your organization’s exposure to secrets-related risks and take proactive steps to mitigate them.
Interactive Learning
Test your knowledge with quizzes designed around secrets management and privileged access management to strengthen your security skills.
Video Tutorials
Watch detailed videos guiding you through configuring resilient secrets workflows and best practices for secure operations.
Community Forum
Join a vibrant community of security professionals to discuss challenges, share insights, and troubleshoot secrets management issues together.


Product Highlights & Comparisons
Explore feature-rich product pages, user guides, and FAQs. Compare top secrets management tools to find the perfect fit for your needs.
Security Alerts & Incident Analysis
Receive timely alerts on vulnerabilities and breaches, with expert analysis on recent incidents and practical lessons learned.
Subscribe for Updates
Sign up for our newsletter to get regular insights, industry news, and expert tips delivered straight to your inbox.
Prerequisites
- A Delinea Platform instance integrated with Secret Server.
- Delinea Platform customers after November 2023 already have Secret Server Cloud integrated.
- Legacy customers of Secret Server Cloud who migrate to the Delinea Platform must integrate the two products.
- Secret Server on-premises customers who purchase the Delinea Platform to use PRA can perform a manual integration.
- An additional Secret Server cloud or on-premises instance that will act as the replica. This instance must not be connected to any other Delinea Platform.
Important: Customers have the option to buy more than one instance of Secret Server, if they want to have multiple replicas.
How Do Resilient Secrets Work
The Resilient Secrets feature copies information from the source Secret Server instance to the replica. Information on the replica Secret Server will be overwritten by the source for anything copied.
The configurations for the Cloud and On-Premises replicas are the same. There is nothing you would need to do differently, configuration wise, when setting up a Cloud replica as opposed to On-Premises and vice-versa. The following diagram represents the flow of data from the source instance to the replica in both the Delinea Platform and Secret Server respectively:
- The Delinea Platform is connected to Secret Server via an encrypted connection.
- Secret Server (Source) is connected to a replica (either Secret Server Cloud Secret Server On-Prem) via an encrypted connection.
- The replica pulls the data package from the Source.
- When the Delinea Platform is available, users can log in to the replica with their Delinea Platform credentials.
- When the Delinea Platform is not available, users can log in to the replica via SAML or via local accounts
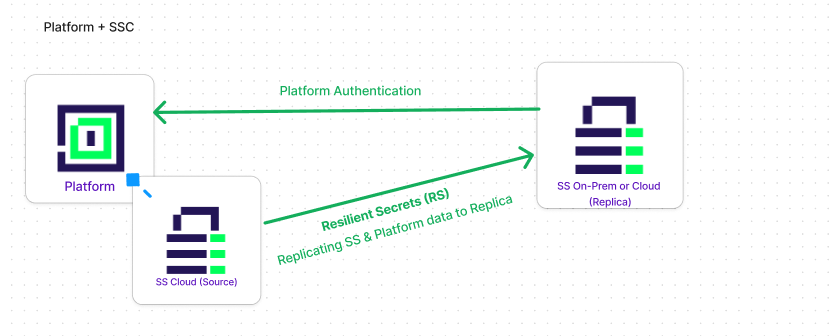
- Note: Only one Delinea Platform and Secret Server Cloud pair is supported
Best Practices
Read-Only Mode:
- Replicas should be in read-only mode during operation because there can only be one source of truth – the Source instance.
Cloud Replicas:
- For a replica Secret Server Cloud, Delinea recommends setting it up in a different geographic region (if both replica and cloud instances are in the same region, an issue impacting that region could disrupt both).
On-Premises Replicas:
- For the replica (Secret Server on-premises), Delinea recommends creating local accounts on that instance so that, in the event of a complete service outage, you will still be able to log in to the replica instance with your local account.
Delinea Platform with Secret Server Cloud and Replica Secret Server Cloud
Cloud replicas respect the user login settings of the Delinea Platform. All configurations are copied from the Delinea Platform to the replica Secret Server Cloud.
In the event of a service outage where the source Secret Server Cloud goes down, users will still be able to log in to the replica Secret Server Cloud tenant using their Delinea Platform credentials.
If you have an external user source (Entra ID, Okta, etc.) for Platform login, those log-ins will also work with the Cloud replica, as long as those sources are still online. If federation providers are down, you can log into Secret Server with your local accounts.
- Local Accounts should be created ahead of time, before a Disaster Recovery event occurs.

Delinea Platform with Secret Server Cloud and ReplicaSecret Server On-Premises
On-premises replicas respect the user login settings of the Delinea Platform. All configurations are copied from the Delinea Platform to the On-Premises replica.
- After logging in to the On-Premises replica with your Delinea Platform credentials, you will still be in the Secret Server On-Premises UI.
Typically, a user could log in to the on-premises replica from its login page using their Delinea Platform credentials, but to prepare for an outage, you must have alternative methods available.

On-Premises Replica Authentication for Delinea Platform-based Login
In the event of a service outage, the Delinea Platform login capability will not be available. To ensure access during an outage, you should prepare an alternative login method, such as configuring SAML for your IdP source, which will allow users to log in with their Delinea Platform credentials. The IdP can be a self-hosted SAML provider (ADFS or other self-hosted option) and does not need to be the same IdP as used by the Delinea Platform.
On-Premises Replica Authentication for Federation-based Login
In the event of a service outage that interrupts federated credential providers (Entra ID, Okta etc.), users will still be able to log in as long as you have:
Configured both source and replica to accept those federation services.
Configured the on-premises replica to use SAML. If the user source is also down, you will only be able to log in with local accounts.
Important: In the event of a service outage, administrators who set up a local account for their on-premises replica will still be able to log in with that account. Any other local accounts you create will also be able to log in.
Frequently Asked Questions
The Primary Secret Server (Source) is connected to the Delinea Platform via an encrypted connection. On the Delinea Platform see (Settings > Secret Server Connection). At this time, only one connection from Delinea Platform to Secret Server is possible.
Since Resilient Secrets is a functionality of Secret Server, every instance of Secret Server needs to be licensed. You can only have one instance of the Delinea Platform and Secret Server, acting as the Source, but you may choose to purchase multiple Replica instances.
There is no special configuration for Cloud or On-Premises replicas to connect to the Delinea Platform. This is done on the Primary (Source) Secret Server. Please refer to Setting Up Resilient Secrets for more information.
No, Secret Server Cloud only supports one Delinea Platform instance at a time. (The Source)
In unified mode your primary instance of Secret Server Cloud (the source) pulls role and permission assignments from platform. This information is then replicated/copied over to the replica Secret Server.
There are two ways you can log in to your Replica instance if the Delinea Platform is not available:
Configure SAML: Configure SAML with your IdP (Identity Providers)
Logging in with local accounts – In the event that everything fails, create “break glass” local accounts on the Replica Secret Server so you can log in when no directory services are available. These local accounts need to be created in advance, before any service outages occur.
Configure SAML with your IdP and/or create local accounts on the Replica instance so you can log in when no directory services are available.
Note: If you create local accounts on the source, they will be copied to the replica.
Resilient Secrets is built upon Secret Server. To have Resilient Secrets on-premises you will need to install Secret Server On-Premises (see downloading Secret Server). If you want Resilient Secrets in the Cloud, you will need to have a second instance of Secret Server Cloud.
Please contact Delinea Sales or Support for purchase questions.
Look for errors in the Resilient Secrets replication logs (Disaster Recovery Log tab on the Replica).
If secrets are skipped, some vital data may be missing.
Run a manual replication by going back a few years or using a date like 1/1/2000 to perform a full sync. If this does not resolve the issue and you cannot determine the errors from the logs, please reach out to support and open a case/work item.
Resilient Secrets are a feature of Delinea's Secret Server designed to enhance disaster recovery and business continuity by replicating secrets data to another instance, either on-premises or in the cloud. This ensures that organizations have continuous access to their secrets and secrets data, even during emergencies, thereby reducing the risk of downtime or disruption in privileged access.
How Resilient Secrets Work

Replication:
Resilient Secrets enable the
replication of secrets data from
a primary Secret Server
instance to a secondary replica
instance. This can be
configured for on-premises to
cloud, cloud to cloud, or cloud
to on-premises environments.

Automated Syncing:
The replication process is
automated, with updates
typically occurring every 15
minutes. This ensures that the
replica instance is always
up-to-date with the latest
secrets data from the primary
instance.

Read-Only Mode:
The replica instance is usually
kept in read-only mode to
maintain data integrity, as there
can only be one source of
truth—the primary instance.

Access During Outages:
In the event of a service outage, users can log in to the replica instance using their Delinea Platform credentials, SAML, or local accounts, ensuring continuous access to critical secrets.
Best Practices

Geographic Distribution:
For cloud replicas, it is recommended to set them up in dierent geographic regions to avoid regional disruptions.
Local Accounts:
For on-premises replicas, creating local accounts ensures access even if directory services are unavailable.


Configuration:
Both cloud and on-premises replicas should be configured similarly to ensure seamless failover.
Features Replicated

Folders and Secrets:
Includes subfolders, permissions, secret templates, and essential secret information.

Roles and Permissions:
All roles and permissions, along with their assignments to users and groups, are replicated.

Metadata:
All metadata on secrets, folders, users, and groups configured for replication are included.

Launchers and Mappings:
All launchers and their fields, mappings to secret templates, and associated secrets are replicated.
Excluded Features
Advanced Settings :
Such as LDAP connection settings, session recordings, and custom reports.
Password Change Information:
Remote password changing and expiration-related settings are not replicated.
Two-Factor Authentication (2FA):
Configuration details for 2FA are not replicated.
“Resilient secrets” are essentially a part of disaster recovery strategies for managing critical data securely and ensuring its availability even in adverse situations. Here’s a comprehensive breakdown of what resilient secrets entail based on the documents you uploaded:

1. Definition and Purpose:
Resilient Secrets (RS) replicate essential data from a primary data source to a secondary data replica. This feature is crucial for ensuring that when the primary source is unreachable, the secondary replica has the most important information and functionality available to maintain minimal operational continuity.

2. Features Replicated:
Only select configurations such as the SSH cipher suite and Platform configuration settings are replicated.
Replicated including their essential information like template, active status, name, and settings.
All launchers are replicated except for their custom icons.
Metadata on secrets, folders, users, and groups configured for replication are replicated.
Replicated including their assignments to users and groups.
Covered.
All sites are replicated with exceptions like site connector and engine information due to encryption constraints.
All are replicated with recommendations to keep users inactive by default to save on licenses and complexities.
3. Exclusions and Exceptions:
Certain features like some configuration settings, custom icons for launchers, and specific encryption-related details are not replicated.
4. Importance in Compliance and Security:
Secret Servers incorporating resilient secrets are designed to adhere to stringent
industry regulations and standards (e.g., HIPAA, PCI DSS, FISMA), providing a
secure architecture for handling sensitive data.
They mitigate risks of insider threats by using granular access controls and
monitoring tools.
5. Disaster Recovery (DR) Mechanism:
The Disaster Recovery feature employs resilient secrets to maintain vital data availability through replicating it across dierent instances. This makes it possible to access critical information during emergencies such as network outages, ensuring that operational integrity and data security are not compromised.
6. Managing Secrets:
Automation tools like Secret Server handle secret management tasks eciently, enforce regular rotation of credentials, maintain backups, and establish robust disaster recovery strategies to ensure reduced downtime and secure restoration of operations.
YouTube
OATH OTP MFA Explained: Easy Setup Guide for Stronger Security
By understanding and implementing resilient secrets, organizations can significantly enhance their disaster recovery preparedness, ensuring that critical data remains secure and accessible in the face of disruptions. This strategy is essential for maintaining compliance, reducing operational risks, and safeguarding sensitive information against unauthorized access
and potential breaches.
About Me
Bert Blevins is a distinguished technology entrepreneur and educator who brings together extensive technical expertise with strategic business acumen and dedicated community leadership. He holds an MBA from the University of Nevada Las Vegas and a Bachelor’s degree in Advertising from Western Kentucky University, credentials that reflect his unique ability to bridge the gap between technical innovation and business strategy.
As a Certified Cyber Insurance Specialist, Mr. Blevins has established himself as an authority in information architecture, with particular emphasis on collaboration, security, and private blockchain technologies. His comprehensive understanding of cybersecurity frameworks and risk management strategies has made him a valuable advisor to organizations navigating the complex landscape of digital transformation. His academic contributions include serving as an Adjunct Professor at both Western Kentucky University and the University of Phoenix, where he demonstrates his commitment to educational excellence and knowledge sharing. Through his teaching, he has helped shape the next generation of technology professionals, emphasizing practical applications alongside theoretical foundations.

In his leadership capacity, Mr. Blevins served as President of the Houston SharePoint User Group, where he facilitated knowledge exchange among technology professionals and fostered a community of practice in enterprise collaboration solutions. He further extended his community impact through director positions with Rotary International Las Vegas and the American Heart Association’s Las Vegas Chapter, demonstrating his commitment to civic engagement and philanthropic leadership. His specialized knowledge in process optimization, data visualization, and information security has proven instrumental in helping organizations align their technological capabilities with business objectives, resulting in measurable improvements in operational efficiency and risk management.
Mr. Blevins is recognized for his innovative solutions to complex operational challenges, particularly in the realm of enterprise architecture and systems integration. His consulting practice focuses on workplace automation and digital transformation, guiding organizations in the implementation of cutting-edge technologies while maintaining robust security protocols. He has successfully led numerous large-scale digital transformation initiatives, helping organizations modernize their technology infrastructure while ensuring business continuity and regulatory compliance. His expertise extends to emerging technologies such as artificial intelligence and machine learning, where he helps organizations identify and implement practical applications that drive business value.

As a thought leader in the technology sector, Mr. Blevins regularly contributes to industry conferences and professional forums, sharing insights on topics ranging from cybersecurity best practices to the future of workplace automation. His approach combines strategic vision with practical implementation, helping organizations navigate the complexities of digital transformation while maintaining focus on their core business objectives. His work in information security has been particularly noteworthy, as he has helped numerous organizations develop and implement comprehensive security frameworks that address both technical and human factors.
Beyond his professional pursuits, Mr. Blevins is an accomplished endurance athlete who has participated in Ironman Triathlons and marathons, demonstrating the same dedication and disciplined approach that characterizes his professional work. He maintains an active interest in emerging technologies, including drone operations and virtual reality applications, reflecting his commitment to staying at the forefront of technological advancement. His personal interests in endurance sports and cutting-edge technology complement his professional expertise, illustrating his belief in continuous improvement and the pursuit of excellence in all endeavors.